Hello Guys,
I wanted to write this article as personal documentation but as well because I wanted to be in most of our partners’ shoes. Most of the time when they want to establish a VPN connection with us and we handover a seemingly complicated AWS VPN generated configuration.
In this tutorial we are going to create a AWS Managed VPN in the California Region us-west-1 and get our VyOS EC2 instance from the us-east-1 to connection to it.
us-east-1 vpc is : 172.20.0.0/16
us-west-1 vpc is : 172.31.0.0/16
Here will be our plan of actions
- Create AWS VPN in California
- Configure the VyOS
Creating AWS Hardware VPN
Each AWS Virtual Private Cloud (VPC), there is a default network. We will just leverage on the default VPC instead of creating a new one. In order to get a create a new AWS VPN, we will need the following:
- Customer Gateway
- Virtual Private Gateway
Customer Gateway
This is an AWS terminology to define the peer ip address. To create a customer gateway , get to the VPC section of AWS , choose the right aws region (california in this tutorial), and below on the left panel of the VPC page, choose click on Customer Gateways under VPN Connections section. We will be using the same VyOS instance we used during our previous VPN. Because we are doing a policy based VPN, we will choose static routing option.
Virtual Private Gateway
This is also another AWS terminology to define the AWS side of the VPN. Probably there are better explanations but this is the simple one I could come up with. A Virtual Private Gateway (VPG) is pretty useless unless attached to the VPC the VPN is meant for. In order to create one, from the VPC page and under the VPN Connections section, click on Virtual Private Gateways and follow the steps below.
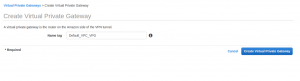
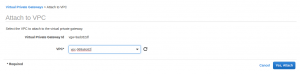
Creating the AWS VPN
With the Customer Gateway and the Virtual Private Gateway we have all we need for our Connection. Click on the VPN Connections link on the left panel to get to the VPN section. Click on Create VPN Connection button to start the process.
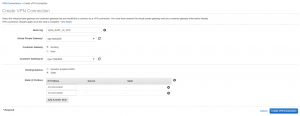
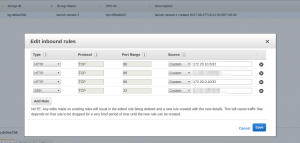
Creating Firewall Rules
We need to accept on boxes behind our AWS VPN traffic from our yet to be configured VyOS VPN side of boxes.
172.20.0.10
172.20.10.5
Generated AWS VPN Configuration
Now to connect to the VPN from our VyOS instance , we needed to generate configuration from the by clicking on the download configuration button. I have downloaded a Generic one. As seen on the screenshot there are 2 separate tunnels with 2 different peer IPs. This configuration is vendor agnostic. They are other vendor specific configuration like for cisco, palo alto, juniper, fortinet, microsoft etc.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 |
Amazon Web Services Virtual Private Cloud VPN Connection Configuration ================================================================================ AWS utilizes unique identifiers to manipulate the configuration of a VPN Connection. Each VPN Connection is assigned a VPN Connection Identifier and is associated with two other identifiers, namely the Customer Gateway Identifier and the Virtual Private Gateway Identifier. Your VPN Connection ID : vpn-1978e141 Your Virtual Private Gateway ID : vgw-9adc82df Your Customer Gateway ID : cgw-7580d930 A VPN Connection consists of a pair of IPSec tunnel security associations (SAs). It is important that both tunnel security associations be configured. IPSec Tunnel #1 ================================================================================ #1: Internet Key Exchange Configuration Configure the IKE SA as follows: Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2. You will need to modify these sample configuration files to take advantage of AES256, SHA256, or other DH groups like 2, 14-18, 22, 23, and 24. The address of the external interface for your customer gateway must be a static address. Your customer gateway may reside behind a device performing network address translation (NAT). To ensure that NAT traversal (NAT-T) can function, you must adjust your firewall !rules to unblock UDP port 4500. If not behind NAT, we recommend disabling NAT-T. - IKE version : IKEv1 - Authentication Method : Pre-Shared Key - Pre-Shared Key : hoT9RIrcpDKXKdSi2xtrGDmg2SsJZ13h - Authentication Algorithm : sha1 - Encryption Algorithm : aes-128-cbc - Lifetime : 28800 seconds - Phase 1 Negotiation Mode : main - Diffie-Hellman : Group 2 #2: IPSec Configuration Configure the IPSec SA as follows: Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24. - Protocol : esp - Authentication Algorithm : hmac-sha1-96 - Encryption Algorithm : aes-128-cbc - Lifetime : 3600 seconds - Mode : tunnel - Perfect Forward Secrecy : Diffie-Hellman Group 2 IPSec Dead Peer Detection (DPD) will be enabled on the AWS Endpoint. We recommend configuring DPD on your endpoint as follows: - DPD Interval : 10 - DPD Retries : 3 IPSec ESP (Encapsulating Security Payload) inserts additional headers to transmit packets. These headers require additional space, which reduces the amount of space available to transmit application data. To limit the impact of this behavior, we recommend the following configuration on your Customer Gateway: - TCP MSS Adjustment : 1379 bytes - Clear Don\'t Fragment Bit : enabled - Fragmentation : Before encryption #3: Tunnel Interface Configuration Your Customer Gateway must be configured with a tunnel interface that is associated with the IPSec tunnel. All traffic transmitted to the tunnel interface is encrypted and transmitted to the Virtual Private Gateway. The Customer Gateway and Virtual Private Gateway each have two addresses that relate to this IPSec tunnel. Each contains an outside address, upon which encrypted traffic is exchanged. Each also contain an inside address associated with the tunnel interface. The Customer Gateway outside IP address was provided when the Customer Gateway was created. Changing the IP address requires the creation of a new Customer Gateway. The Customer Gateway inside IP address should be configured on your tunnel interface. Outside IP Addresses: - Customer Gateway : 34.230.141.57 - Virtual Private Gateway : 52.53.87.61 Inside IP Addresses - Customer Gateway : 169.254.9.130/30 - Virtual Private Gateway : 169.254.9.129/30 Configure your tunnel to fragment at the optimal size: - Tunnel interface MTU : 1436 bytes #4: Static Routing Configuration: To route traffic between your internal network and your VPC, you will need a static route added to your router. Static Route Configuration Options: - Next hop : 169.254.9.129 You should add static routes towards your internal network on the VGW. The VGW will then send traffic towards your internal network over the tunnels. IPSec Tunnel #2 ================================================================================ #1: Internet Key Exchange Configuration Configure the IKE SA as follows: Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2. You will need to modify these sample configuration files to take advantage of AES256, SHA256, or other DH groups like 2, 14-18, 22, 23, and 24. The address of the external interface for your customer gateway must be a static address. Your customer gateway may reside behind a device performing network address translation (NAT). To ensure that NAT traversal (NAT-T) can function, you must adjust your firewall !rules to unblock UDP port 4500. If not behind NAT, we recommend disabling NAT-T. - IKE version : IKEv1 - Authentication Method : Pre-Shared Key - Pre-Shared Key : GW3lkkz3B_ekriwF.Vr.4U.QVGPh0vwe - Authentication Algorithm : sha1 - Encryption Algorithm : aes-128-cbc - Lifetime : 28800 seconds - Phase 1 Negotiation Mode : main - Diffie-Hellman : Group 2 #2: IPSec Configuration Configure the IPSec SA as follows: Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24. - Protocol : esp - Authentication Algorithm : hmac-sha1-96 - Encryption Algorithm : aes-128-cbc - Lifetime : 3600 seconds - Mode : tunnel - Perfect Forward Secrecy : Diffie-Hellman Group 2 IPSec Dead Peer Detection (DPD) will be enabled on the AWS Endpoint. We recommend configuring DPD on your endpoint as follows: - DPD Interval : 10 - DPD Retries : 3 IPSec ESP (Encapsulating Security Payload) inserts additional headers to transmit packets. These headers require additional space, which reduces the amount of space available to transmit application data. To limit the impact of this behavior, we recommend the following configuration on your Customer Gateway: - TCP MSS Adjustment : 1379 bytes - Clear Don't Fragment Bit : enabled - Fragmentation : Before encryption #3: Tunnel Interface Configuration Your Customer Gateway must be configured with a tunnel interface that is associated with the IPSec tunnel. All traffic transmitted to the tunnel interface is encrypted and transmitted to the Virtual Private Gateway. The Customer Gateway and Virtual Private Gateway each have two addresses that relate to this IPSec tunnel. Each contains an outside address, upon which encrypted traffic is exchanged. Each also contain an inside address associated with the tunnel interface. The Customer Gateway outside IP address was provided when the Customer Gateway was created. Changing the IP address requires the creation of a new Customer Gateway. The Customer Gateway inside IP address should be configured on your tunnel interface. Outside IP Addresses: - Customer Gateway : 34.230.141.57 - Virtual Private Gateway : 54.153.98.102 Inside IP Addresses - Customer Gateway : 169.254.11.42/30 - Virtual Private Gateway : 169.254.11.41/30 Configure your tunnel to fragment at the optimal size: - Tunnel interface MTU : 1436 bytes #4: Static Routing Configuration: To route traffic between your internal network and your VPC, you will need a static route added to your router. Static Route Configuration Options: - Next hop : 169.254.11.41 You should add static routes towards your internal network on the VGW. The VGW will then send traffic towards your internal network over the tunnels. |
Configuring VPN on VyOS
We will be using the same VyOS box used on previous VPN blog post so I will skip the setup part of this. So this part assumes you have a little knowledge on how to get you VyOS box up and running in an AWS environment.
Creating Virtual Interfaces
We will need to create virtual interfaces to map to each of AWS VPN Virtual Private Gateways. After login on VyOS we will to type configure to start the configuration mode of it.
|
1 2 3 4 5 6 7 |
set interfaces vti vti0 description "VyOSEAST_AWSWEST_VPN tunnel 1" set interfaces vti vti0 address 169.254.9.129/30 # this is the IP range given by AWS inside VPG IP for tunnel 1 set interfaces vti vti0 mtu 1436 set interfaces vti vti1 description "VyOSEAST_AWSWEST_VPN tunnel 2" set interfaces vti vti1 address 169.254.11.41/30 # this is the IP range given by AWS inside VPG IP for tunnel 2 set interfaces vti vti1 mtu 1436 |
Creating IKE and ESP Settings
AWS support a wide variety of proposals for encryption aes128, aes256, 3des and hashing algorithm like md5, sha1 or sha2. We will be using aes256 for encryption and sha1 for hashing. Still in configuration mode enter the following commands.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 lifetime 28800 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 proposal 1 dh-group 2 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 proposal 1 encryption aes256 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 proposal 1 hash sha1 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 dead-peer-detection action restart set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 dead-peer-detection interval 15 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 dead-peer-detection timeout 30 set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 lifetime 3600 set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 mode tunnel set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 pfs enable set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 proposal 1 encryption aes256 set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 proposal 1 hash sha1 |
Creating IPSEC Configuration
Now that we have all we need to start configuring our peers. Let’s step into vpn ipsec configuration. Still in vyos configuration mode let’s input the following commands
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
# set vpn ipsec ipsec-interfaces interface eth0 set vpn ipsec nat-traversal enable edit vpn ipsec site-to-site peer 52.53.87.61 set description "VyOS US EAST 1A Region to AWS Hardware VPN US WEST 1 tunnel 1" set authentication mode pre-shared-secret set authentication pre-shared-secret hoT9RIrcpDKXKdSi2xtrGDmg2SsJZ13h set connection-type initiate set ike-group IKE-AES256-SHA1-LT28800 set local-address 172.20.0.5 set vti bind vti0 set vti esp-group ESP-AES256-SHA1-LT3600 top edit vpn ipsec site-to-site peer 54.153.98.102 set description "VyOS US EAST 1A Region to AWS Hardware VPN US WEST 1 tunnel 2" set authentication mode pre-shared-secret set authentication pre-shared-secret GW3lkkz3B_ekriwF.Vr.4U.QVGPh0vwe set connection-type initiate set ike-group IKE-AES256-SHA1-LT28800 set local-address 172.20.0.5 set vti bind vti1 set vti esp-group ESP-AES256-SHA1-LT3600 top |
Creating static routes
We will be reaching out 2 boxes behind AWS VPN their IPs are:
172.31.7.4
172.31.15.235
We are creating static routes on the VyOS to forward any traffic to those IPs to go through the virtual interfaces/ Virtual Private Gateway. In configuration mode, issue the following commands:
|
1 2 3 4 5 6 7 |
# set protocols static interface-route 172.31.7.4/32 next-hop-interface vti0 distance 1 set protocols static interface-route 172.31.7.4/32 next-hop-interface vti1 distance 2 set protocols static interface-route 172.31.15.235/32 next-hop-interface vti0 distance 1 set protocols static interface-route 172.31.15.235/32 next-hop-interface vti1 distance 2 |
Below is the full configuration
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 |
set interfaces vti vti0 description "VyOSEAST_AWSWEST_VPN tunnel 1" set interfaces vti vti0 address 169.254.9.129/30 set interfaces vti vti0 mtu 1436 set interfaces vti vti1 description "VyOSEAST_AWSWEST_VPN tunnel 2" set interfaces vti vti1 address 169.254.11.41/30 set interfaces vti vti1 mtu 1436 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 lifetime 28800 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 proposal 1 dh-group 2 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 proposal 1 encryption aes256 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 proposal 1 hash sha1 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 dead-peer-detection action restart set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 dead-peer-detection interval 15 set vpn ipsec ike-group IKE-AES256-SHA1-LT28800 dead-peer-detection timeout 30 set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 lifetime 3600 set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 mode tunnel set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 pfs enable set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 proposal 1 encryption aes256 set vpn ipsec esp-group ESP-AES256-SHA1-LT3600 proposal 1 hash sha1 set vpn ipsec ipsec-interfaces interface eth0 set vpn ipsec nat-traversal enable edit vpn ipsec site-to-site peer 52.53.87.61 set description "VyOS US EAST 1A Region to AWS Hardware VPN US WEST 1 tunnel 1" set authentication mode pre-shared-secret set authentication pre-shared-secret hoT9RIrcpDKXKdSi2xtrGDmg2SsJZ13h set connection-type initiate set ike-group IKE-AES256-SHA1-LT28800 set local-address 172.20.0.5 set vti bind vti0 set vti esp-group ESP-AES256-SHA1-LT3600 top edit vpn ipsec site-to-site peer 54.153.98.102 set description "VyOS US EAST 1A Region to AWS Hardware VPN US WEST 1 tunnel 2" set authentication mode pre-shared-secret set authentication pre-shared-secret GW3lkkz3B_ekriwF.Vr.4U.QVGPh0vwe set connection-type initiate set ike-group IKE-AES256-SHA1-LT28800 set local-address 172.20.0.5 set vti bind vti1 set vti esp-group ESP-AES256-SHA1-LT3600 top set protocols static interface-route 172.31.7.4/32 next-hop-interface vti0 distance 1 set protocols static interface-route 172.31.7.4/32 next-hop-interface vti1 distance 2 set protocols static interface-route 172.31.15.235/32 next-hop-interface vti0 distance 1 set protocols static interface-route 172.31.15.235/32 next-hop-interface vti1 distance 2 commit save |
Persist Configuration
In VyOS, changes made to the configuration should be committed and then save to file. That can be done with the following:
|
1 2 3 4 |
# commit save exit |
Verification
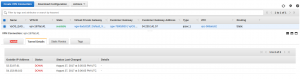
Let’s check VPN status on the VyOS side. This command is done in normal mode show vpn ipsec sa
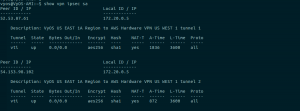
On the AWS VPN side as well let’s verify on the VPN page tunnel tab status of our VPN
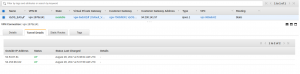
Testing Connectivity
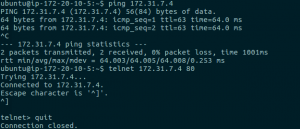
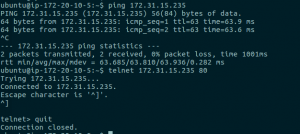
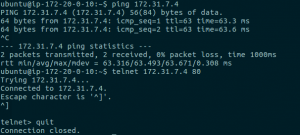
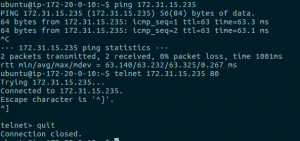
Obviously I have skipped routing at the aws route table level. I did automatic propagation on the AWS VPN side and did it manually on the VyOS side.
Next time we will look at similar setup but this time with dynamic routing. I hope this was useful
These configurations are route-based vpn configs… aren’t they? The name of the document is “How to establish a policy based VPN connection to AWS Hardware VPN”. If you are creating virtual tunnel interfaces and using them for routing traffic over the tunnel, that is route-based. I am so confused now.
Hi Heath,
Yeah, it seems confusing but with regards to AWS Managed VPN, this the way I gotten my own to work because their route based configuration is with BGP. You can read on it here http://www.mycodingpains.com/establish-route-based-vpn-connection-aws-hardware-vpn/